Situatie
Solutie
DLP solutions can be used to classify and prioritize data security. You can also use these solutions to ensure access policies meet regulatory compliance, including HIPAA, GDPR, and PCI-DSS. DLP solutions can also go beyond simple detection, providing alerts, enforcing encryption, and isolating data.
Some other common features of DLP solutions are:
- Monitoring – provide visibility into who is accessing data and systems, and from where
- Filtering – filter data streams to restrict suspicious or unidentified activity
- Reporting – logging and reports helpful for incident response and auditing
- Analysis – identify vulnerabilities and suspicious behavior, and provide forensic context to security teams
This is part of an extensive series of guides about data security.
In this article, you will learn:
- What is DLP?
- DLP use cases
- Trends driving DLP adoption
- Building your data loss prevention policy
- 3 reasons for implementing a data loss prevention policy
- Tips for creating a successful DLP policy
- 4 DLP best practices
- Data classification must be central to DLP execution
- Establish policies upfront
- How to start
- Know that DLP technology has its limitations
- Complementing DLP with next-gen security analytics
There are two main technical approaches to DLP:
- Context analysis looks only at metadata or other properties of the document, such as header, size, and format.
- Content awareness involves reading and analyzing a document’scontent to determine if it includes sensitive information.
Modern DLP solutions combine both of these approaches. At the first stage, DLP examines the context of a document to see if it can be classified. If context is insufficient, it explores within the document using content awareness.
There are several techniques commonly used for content awareness:
- Rule-based – analyzing a document’s content using certain rules or regular expressions, for example, searching for credit card numbers or social security numbers. This approach is very effective as an initial filter, because it is easy to configure and process, but it is usually combined with additional techniques.
- Dictionaries – by combining the use of dictionaries, taxonomies, and lexical rules, the DLP solution can identify concepts that indicate sensitive information in unstructured data. This requires careful customization to each organization’s data.
- Exact data matching – creates a “fingerprint” of the data, and searches for exact matches in a database dump or currently running database. However, creating a data dump or accessing live databases can negatively affect performance — one drawback of this technique.
- Exact file matching – creates a hash of the entire file, and looks for files that match this hash. This technique is very accurate, but cannot be used for files with multiple versions.
- Partial document match – can identify files where there is a partialmatch; for example, the same form filled out by different users.
- Statistical analysis – can use machine learning algorithms for Bayesian analysis to identify content that violates a policy or contains sensitive data. The effectiveness of these techniquescan be increased by feedingmore labeled data to the algorithm for training.
Solutions can be helpful in a variety of use cases, including:
- Ensuring compliance for personal information – If your organization needs to comply with regulations like GDPR or HIPAA, DLP can help identify and classify sensitive information, add required security controls, and help you set up monitoring and reporting to protect the data.
- Preventing data leakage user endpoints – DLP solutions can protect data stored on endpoints such as mobile devices and laptops, which are at high risk because they connect to unsecured networks, and may be lost or stolen. DLP can identify suspicious events on a device and alert security teams that there is a risk of data loss.
- Data discovery – DLP can continuously discover and classify the organization’s sensitive data, whether it is stored on endpoints, storage systems, or servers. It can also provide visibility into who is using the data and what actions they are performing.
- Prevent data exfiltration – Sophisticated attackers carry out targeted cyber attacks, usually with the aim of stealing sensitive data. In the event of a breach, DLP solutions can prevent data exfiltration by identifying a suspicious data transfer, blocking it, and alerting security teams.
- Central management of sensitive data – DLP solutions provide central control over all sensitive data assets, enabling you to set policies, grant or revoke access, and generate compliance reports.
Trends influencing DLP
- Growth of the CISO role – Organizations’ chief information security officers (CISOs) are responsible for data leaks, and use a DLP policy as a tool to gain visibility and report on business information.
- Evolving compliance requirements – New regulations are constantly being introduced. After GDPR in Europe, many similar privacy laws around the world followed, including the California Consumer Privacy Act (CCPA) and Brazil’s Lei Geral de Proteçao de Dados (LGPD). DLP policies can help comply with these new regulations and others like them.
- There are more opportunities now for your data to be at risk – Businesses today use tools that are difficult to monitor, such as supply chain networks and cloud storage. This increases the complexity of data protection. Knowing exactly which data crosses organizational boundaries is critical to preventing misuse.
- Data exfiltration is a growing risk – Sensitive data is an attractive target for attackers. The number of attempted and successful data breaches at organizations of all sizes is rapidly growing, and has seen a sharp incline since the beginning of the pandemic-driven shift to remote working.
- Insider threats – Data loss is increasingly caused by malicious insiders, compromised privileged accounts, or accidental data sharing by employees.
- Stolen data is worth more – The dark web allows adversaries to buy and sell stolen information. Data theft is a profitable business.
- More data to steal – The scope and definition of sensitive data has broadened over time. Sensitive data now includes intangible assets, for example, business methodologies and pricing models.
- Security talent shortage – Many businesses are finding it difficult to fill security-related roles. In recent surveys by ESG and ISSA, 43% of organizations surveyed reported being affected by the talent shortage. This makes automated tools like DLP more attractive.
Modern data storage can be accessed from remote locations and through cloud services.Llaptops and mobile phones contain sensitive information, and these endpoints are often vulnerable to hacking, theft, and loss. It is becoming increasingly difficult to ensure that company data is secure, making DLP a critical strategy.
- Compliance – Businesses are subject to mandatory compliance standards imposed by governments (such as HIPAA, SOX, PCI DSS). These standards often stipulate how businesses should secure Personally Identifiable Information (PII) and other sensitive data. A DLP policy is a basic first step to compliance, and most DLP tools are built to address the requirements of common standards.
- Intellectual property and intangible assets – An organization may have trade secrets, other strategic proprietary information, or intangible assets, such as customer lists and business strategies. Loss of this type of information can be extremely damaging, making it a direct target for attackers and malicious insiders. A DLP policy can help identify and safeguard critical information assets.
- Data visibility – Implementing a DLP policy can provide insight into how stakeholders use data. In order to protect sensitive information, organizations must first know that it exists, where it resides, who accessesit, and for what purposes it is used.
Tips for creating a successful DLP policy
- Classify and interpret data – Identify which information needs to be protected by evaluating risk factors and its level of vulnerability. Invest in classifying and interpreting data because this is the basis for implementing a data protection policy that suits your organization’s needs.
- Allocate roles – Clearly define the role of each individual involved in the data loss prevention strategy.
- Begin by securing the most sensitive data – Start by selecting a specific kind of information to protect, which represents the biggest risk to the business.
- Automate as much as possible – The more DLP processes are automated, the more broadly you’ll be able to deploy them in your organization. Manual DLP processes are inherently limited in their scope and the amount of data they can cover.
- Use anomaly detection – Some modern DLP tools use machine learning and behavioral analytics, rather than simple statistical analysis and correlation rules, to identify abnormal user behavior. Each user and group of users is modeled with a behavioral baseline, allowing accurate detection of data actions that might represent malicious intent.
- Involve leaders in the organization – Management is key to making DLP work, because policies are worthless if they are unable to be enforced at the organizational level.
- Educate stakeholders – Simply putting a DLP policy in place is not enough. Invest in making stakeholders and users of data aware of the policy, its significance, and what they need to do to safeguard your organization’s data.
- Documenting DLP strategy – Documenting the DLP policy is required by several compliance standards. It also provides clarity around policy requirements and enforcement, both at the individual and organizational level.
- Establish metrics – Measure DLP effectiveness using metrics like percentage of false positives, number of incidents and Mean Time to Response.
- Don’t save unnecessary data – A business should only use, save, and store essential information. If it’s not needed, remove it; data that was never stored can nevergo missing.
1. Data classification must be central to DLP execution
Before implementing a DLP solution, pay special attention to the nature of your company’s sensitive information, and how it flows from one system to another. Identify how information is transferred to its consumers; this will reveal transmission paths and data repositories. Classify sensitive data by categorizing it with labels, such as “employee data,” “intellectual property,” and “financial data.”.
Investigate and record all data exit points. Organizational processes may not be documented, and not all data movement happens as part of a routine practice. Engage IT and business staff in the early stages of policy development. This stage of the process should include identifying:
- Data categories that have been singled out
- Steps that need to be implemented to combat malpractice
- Future growth of the DLP strategy
- Steps that need to be taken if there is any unusual activity
Before putting the DLP strategy into practice, it is essential to establish incident management processes and ensure they are practical for eachdata category.
The first step to implementing DLP is monitoring organizational data. This lets you anticipate and refine the effect that the DLP may have on organizational culture and operations. By blocking sensitive information too soon, you may negatively impactcentral business activities.
DLP provides a lot of information, such as the transmission path and location of all sensitive information, which can be overwhelming. Resist the temptation to try to solve all of your data protection issues at once.
A good way to start your DLP implementation is with the low hanging fruit. Establish rules and ensure they are continually considered and improved. Involve all relevant stakeholders and ensure they provide feedback on new data types, formats, or transmission paths that are not listed in the current DLP strategy or not currently protected.
4. Know that DLP technology has its limitations
- Encryption – DLP tools can only examine encrypted information that they initially decrypt. If users encrypt data with keys that the DLP system operators can’t access, the information is invisible.
- Rich media – DLP tools are generally not useful when working with rich media such as images and video, because they cannot parse and classify their content.
- Mobile – DLP solutions cannot track all types of modern mobile communication, likemessages sent from a user’s private mobile device.
DLP solutions are great at monitoring data flows and securing against known threat patterns. However, malicious insiders and sophisticated attackers can act in ways that are unpredictable, or that evade DLP security rules. A category of security tools called user and entity behavior analytics (UEBA) can help.
UEBA tools establish a behavioral baseline for individual users, applications, network devices, IoT devices, or peer groupings of any of these. Using machine learning, they can identify abnormal activity for a specific entity or group of entities, even if it doesn’t match any known threat or pattern. This can complement traditional DLP solutions, alerting security teams of data-related incidents that have slipped past DLP rules.
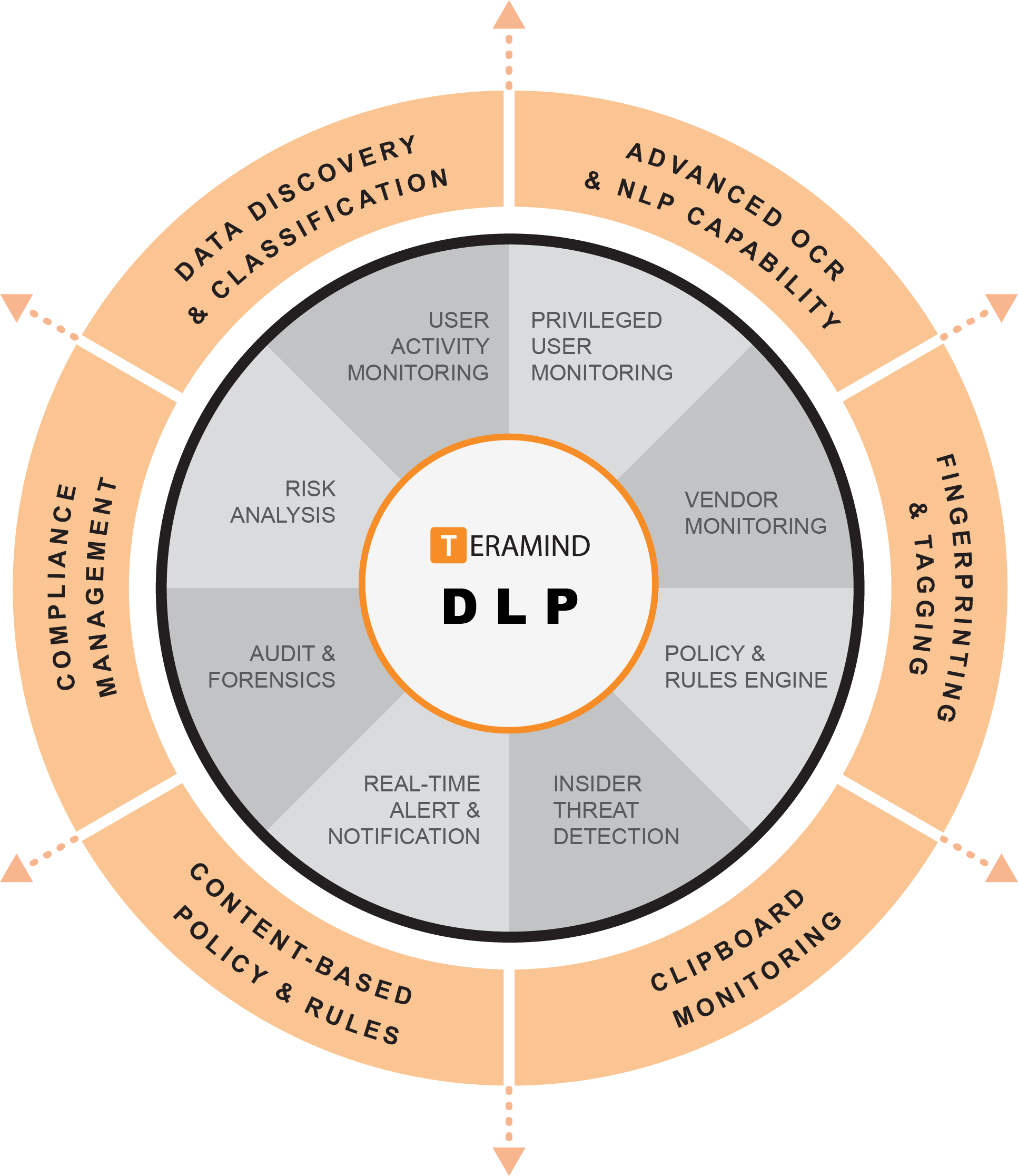
Teramind’s ‘user-centric’, endpoint Data Loss Prevention solution goes beyond traditional DLP approaches. Teramind’s DLP services adds intelligent behavioral analysis to identify human factors.
Human factors may include malicious intent, errors or accidents. With Teramind’s data loss prevention software you can implement effective protection against data breaches and other exfiltration attempts. Teramind DLP software provides the best return of investment for organizations of any size. The DLP software is designed to assist SMBs, enterprises and the public sector address data loss, cybersecurity and insider threats.
Additionally, Teramind’s compliance management features help you conform with compliance regulations including GDPR, HIPAA, PCI DSS, and ISO 27001.

Leave A Comment?