Situatie
Solutie
The primary focus of a DoS attack is to oversaturate the capacity of a targeted machine, resulting in denial-of-service to additional requests. The multiple attack vectors of DoS attacks can be grouped by their similarities.
DoS attacks typically fall in 2 categories:
Buffer overflow attacks
An attack type in which a memory buffer overflow can cause a machine to consume all available hard disk space, memory, or CPU time. This form of exploit often results in sluggish behavior, system crashes, or other deleterious server behaviors, resulting in denial-of-service.
Flood attacks
By saturating a targeted server with an overwhelming amount of packets, a malicious actor is able to oversaturate server capacity, resulting in denial-of-service. In order for most DoS flood attacks to be successful, the malicious actor must have more available bandwidth than the target.
The distinguishing difference between DDoS and DoS is the number of connections utilized in the attack. Some DoS attacks, such as “low and slow” attacks like Slowloris, derive their power in the simplicity and minimal requirements needed to them be effective.
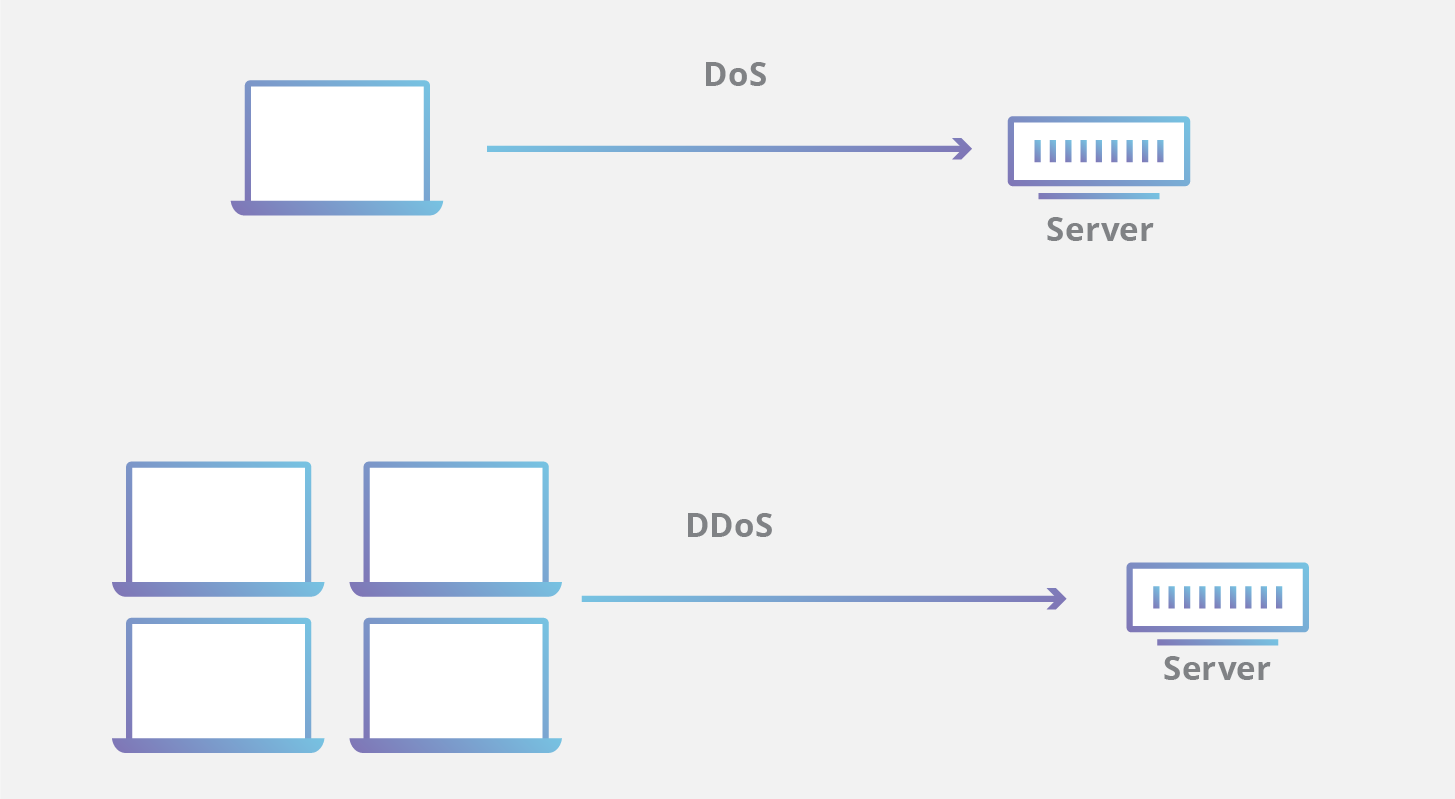
DoS utilizes a single connection, while a DDoS attack utilizes many sources of attack traffic, often in the form of a botnet. Generally speaking, many of the attacks are fundamentally similar and can be attempted using one more many sources of malicious traffic. Learn how Cloudflare’s DDoS protection stops denial-of-service attacks.
- What is meant by DoS: Denial of Service Attack Definition
- What is the primary goal of a DoS attack?
- DOS Attack types
- Denial of Service in Network Security
- Denial of service attack example
- Denial of Service Attack prevention
1. What is meant by DoS: Denial of Service Attack Definition
DoS attack full form or dos definition indicates denial of service attack. Hence, the dos attack meaning signifies specific attacks that are carried out by flooding the target systems with traffic or by sending it malicious data that might provoke the target resource to fail or even completely crash. Cyber-intruders typically target the network or operating system with superfluous requests to overload the systems. Such attempts of overloading the network result in a denial of legitimate services to genuine users.
The denial of service comes as an attack in the information technology sector and causes a huge loss in money, time, and depriving information servers. While some of the DoS attacks are carried out to only disrupt the targets access to a network or resource, others are designed to isolate the resource and make it completely inaccessible for the target.
Well-established banking, commerce, media companies, or government and trade organizations are usually prey to DoS attack cybercriminals.
2. What is the primary goal of a DoS attack?
The primary goal of the Denial of Service attack is to deprive the legitimate targets users of accessibility to their resources or machine. In other words, it is an attack targeting the availability of web applications. DoS attacks are different from other kinds of cyber-attacks as DoS attacks’ primary goal is not to steal/destroy/alter the information in the intended target system’s data but to merely slow down or take down the resources.
Even though the attack does not result in any harm to your data stored in the system, it still is time-consuming as some of the DoS attacks may last from a couple of minutes to hours and in extreme cases, even days. To retrieve its resources, the organization may also end up suffering from significant financial loss. Attackers’ motivation to carry out a DoS attack is diverse, ranging from simply having fun to financial gain and even hacktivism. All sectors can be victims of a Denial of Service/DoS attack, be it gaming, banking, e-commerce websites of any size in any location.
3. DoS Attack types
There are numerous types of Denial of Service attacks. Not all networks and computer systems are attacked in the same way. Thus, cyber criminals must be creative and find loopholes and exploit the system/resource configuration’s possible vulnerabilities. The two broad types of DoS attacks, based on the number of systems used to launch the attack, are
- Non-distributed Denial of Service attack
- Distributed Denial of Service attack/DDoS
A non-distributed DoS attack is defined as using a single machine’s resources to exhaust those of the targeted machine to deprive access to its resources/data. As large and robust web servers will be unaffected by DoS attacks from a single machine, attackers make use of DDoS/Distributed Denial of Service. This is where multiple computer systems continuously and simultaneously attack the target to exhaust their resources. A DDoS is also difficult to trace back to the attacker as the attack has multiple source points.
Based on the DoS attack outcome, there are two types: buffer overflow attacks and flood attacks.
- Buffer Overflow Attacks- An attack in which the perpetrator sends in more traffic to the target than the system can handle. It causes a memory buffer overflow and causes the consumption of all available hard disk space, memory, or CPU time, which further results in sluggish behavior, crashes, and ultimately Denial of Service.
- Flood Attacks- This attack is accomplished by overwhelming the target server with more packets than the server can handle, resulting in DoS. The malicious actor must have more bandwidth available than the target server to complete the attack.
Some of the popular kinds of flood attacks are ICMP flood and SYN flood.
- ICMP stands for Internet Control Message Protocol, also known as ping flood attack. This denial-of-service attack is accomplished by overwhelming the target with ICMP/ping packets more than it can respond to efficiently, and hence denial-of-service occurs.
- SYN Flood attack is when the perpetrator continuously sends connection requests to the target server but never finalizes the connection. The server then spends a lot of time and resources on these connection requests, making it unresponsive to legitimate traffic.
4. Denial of Service in Network Security
DoS attacks can cause the following problems in networks:
- Ineffective services
- Inaccessible services
- Interruption of network traffic
- Connection interference
5. Denial of service attack example
You visit an e-commerce website to shop for clothing, and your computer sends a small information packet to the website simply saying ‘hello.’ This packet basically says to the website, “Hello, I’d like to visit your website, please let me in.” When the website receives this, it sends back another packet saying, “Okay, are you real?” Your computer responds by saying, “yes,” and the connection is established, and now you can explore the website and purchase your clothes.
In a DoS attack, the offender’s system is altered to send not one but hundreds and thousands of packets of introduction information. Since the server cannot determine which ones are fake and which ones are legitimate, they send out the usual packet of information saying, “Okay, are you real?” to confirm that. The server waits up to 1 minute for the computer to respond, and when it gets no reply, the server then proceeds to disconnect from the systems requests.
Post this, the computer executing the attack sends in another batch of fake request packets, and so on. This is done until the server ultimately shuts down and the offender’s denial of Service attack is successful. This is a DoS attack example.
6. Denial of Service Attack prevention
Any organization relying on its website to carry out their business must be aware of DoS attacks and how to prevent them. The quicker you can stop the attack, the lesser the damage.
DoS attack prevention methods-
- Use software for the early detection of DoS attacks. Big-shot companies often use anti-DDoS software technology to recognize legitimate spikes in network traffic and a DDoS attack.
- Have your ISP on standby- Notify your Internet Service Providers as soon as you realize your server is under a DoS attack, meaning ISPs can help reroute the traffic to another server to keep yours safe. A backup ISP is also a good idea. Services that can reroute the huge DDoS traffic among a network of servers can also help to render an attack ineffective.
- Blackhole routing is when the massive amounts of traffic your server is receiving is rerouted onto a null path, also known as a black hole. The only disadvantage of this prevention method is that all the traffic is redirected into the black hole, including legitimate traffic.
- Firewalls and routers- Update your firewalls and routers regularly with the latest security patches to reject fake traffic and accept legitimate traffic efficiently.
- Front-end hardware-Front-end hardware combined with network server can help screen information packets into priority, regular, and dangerous before the traffic reaches the server. This also efficiently blocks threatening data out of the server.

Leave A Comment?