Situatie
In this post we’ll deal with one of the most undervalued and semi-unknown features of Internet Information Services, better known as IIS, the web server shipped with most Windows client and servers distributions – from Windows 95 to Windows 10 and Windows Server 2019: the IP and Domain Restrictions role service, which allows the system administrator to allow or deny access to the web server, web sites, folders, or files through various rules that can be configured for remote IP addresses or based on the domain name.
Solutie
Pasi de urmat
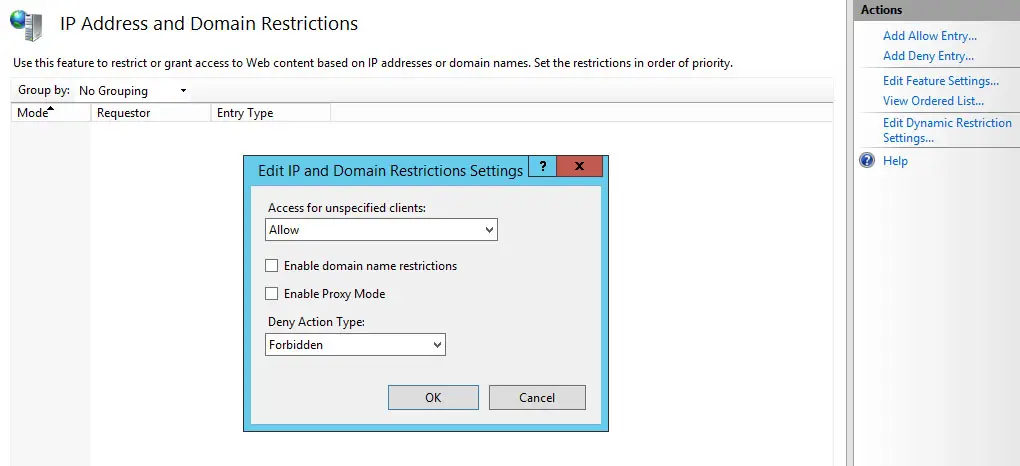
IIS allows restricting access to a website to a specific list of IP addresses. This possibility is managed through the IP Address and Domain Restrictions built-in feature, which supports two alternative usage modes:
- Whitelist, i.e. to prevent access to any external IP address with the exception of a list of authorized IPs.
- Blacklist, i.e. to authorize access to any external IP address with the exception of a list of blocked IPs.
Such a feature is made accessible through the IIS Manager GUI
Using the web.config file
The IP Address restrictions can be configured within the web.config file of any single website in the following way:
<system.webServer>
<system.webServer>
<security>
<ipSecurity allowUnlisted=”false” enableProxyMode=”true”>
<add ipAddress=”90.98.92.0″ subnetMask=”255.255.255.0″ allowed=”true” />
<add ipAddress=”90.69.30.186″ allowed=”true” />
</ipSecurity>
</security>
</system.webServer>
</system.webServer>
Notice how the syntax and attributes are the same as the applicationHost.config file – the only missing thing here is the <location> tag since the location is implicit (the current website).
The first time you implement the <ipSecurity> tag inside a web.config file you may get the following error:
Config Error: This configuration section cannot be used at this path. This happens when the section is locked at a parent level. Locking is either by default (overrideModeDefault = “Deny”), or set explicitly by a location tag with overrideMode = “Deny” or the legacy allowOverride = “false”.
This error usually occurs when inserting the <ipSecurity> tag inside the web.config file without first allowing/enabling this configuration option to be overridden globally (the default behavior is Deny).
The solution is to edit the applicationHost.config file and change the defaut behavior from “Deny” to “Allow” in the following way:
|
1
|
<section name=“ipSecurity” overrideModeDefault=“Allow “/>
|
If you are using IIS, the applicationHost.config file path is the following one which we have mentioned early on:
- C:\Windows\system32\inetsrv\config\applicationHost.config
However, if you are using IIS Express (which is rather common if you are a Visual Studio developer), and you are getting the above 500.19 error due to the “denied” usage of the <ipSecurity> tag, you might want to also check out the following paths:
- C:\Users\<username>\Documents\IISExpress\config\applicationHost.config (IIS Express global configuration path)
- C:\Projects\<ProjectFolder>\ .vs\<ProjectName>\config\applicationHost.config (IIS Express project-specific path).

Leave A Comment?