Situatie
Solutie
INTRODUCTION:
The phrases “threat” and “risk” are sometimes mistaken and used interchangeably with “vulnerability.” In cybersecurity, though, it’s critical to distinguish between danger, vulnerability, and risk. Before diving into each concept in detail look at the easier version to gain a well-rounded understanding of what actually these terms mean. In addition to threat, risk and vulnerability is ‘asset’ that plays a vital role in getting meaning out of all the three terms.
People, property, and information are all assets. Employees and clients, as well as other invited individuals such as contractors or visitors, may be present. Property assets include both tangible and intangible assets with monetary worth. Reputation and private knowledge are examples of intangible assets. Databases, software code, essential corporate records, and a variety of other intangible commodities are examples of information.
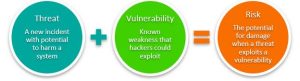
A threat is anything that can use a vulnerability to obtain access to, harm, or destroys an asset, whether deliberately or inadvertently. We’re attempting to defend against danger.
Weaknesses or flaws in a security programme that can be exploited by attackers to obtain unauthorised access to an asset are known as vulnerabilities.
Risk is the possibility of an asset being lost, damaged, or destroyed as a result of a threat exploiting a vulnerability. The junction of assets, threats, and vulnerabilities is known as risk.
What does it mean to be vulnerable?
It’s a vulnerability that empowers a bad actor to get hold of and manipulate your assets. A flaw in your hardware, software, or operations is referred to as a vulnerability.
A vulnerability is a flaw in hardware, software, personnel, or processes that threat actors can use to achieve their objectives. Cyber vulnerabilities are occasionally formed as a result of cyberattacks rather than network misconfigurations. It can also be triggered if an employee unintentionally downloads a virus or falls victim to a social engineering attempt.
Vulnerability is a flaw or breach in your defences.
Vulnerability management assists in pinpointing, detailing and rebuilding security. A zero-day vulnerability is a vulnerability for which a remedy is not yet known. Testing for vulnerabilities is critical to ensuring the continued security of your systems. By identifying weak points, you can develop a strategy for quick response. Here are some questions to ask when determining your security vulnerabilities:
- Is your data backed up and stored in a secure off-site location?
- Is your data stored in the cloud? If yes, how exactly is it being protected from cloud vulnerabilities?
- What kind of network security do you have to determine who can access, modify, or delete information from within your organization?
- What kind of antivirus protection is in use? Are the licenses current? Is it running as often as needed?
- Do you have a data recovery plan in the event of a vulnerability being exploited?
What does it mean by threat?
Any hazard that has the potential to damage or steal data, disrupt operations, or cause harm, in general, is considered a threat. Malware, phishing, data breaches, and even rogue employees are all potential threats.
Individuals or groups with a range of backgrounds and goals, known as threat actors, make threats. To design effective mitigations and make informed cybersecurity judgments, it’s critical to first understand the risks. Information on threats and threat actors is known as threat intelligence.
A threat is Something that has the potential to harm or destroy an asset.
Types of Threats
- Intentional risks – Malware, ransomware, phishing, harmful code, and obtaining user login credentials incorrectly are all instances of purposeful dangers. Bad actors utilise these behaviours or ways to breach a security or software system.
- Unintentional risks – Human mistake is frequently blamed for unintentional threats such as failing to update the firewall or anti-virus software, which might make the system more vulnerable.
- Natural catastrophes, often known as natural risks, like floods, hurricanes, tornadoes, earthquakes, and so on aren’t usually linked to cybersecurity, they are unexpected and can do significant harm to your assets.
What is risk?
Risk is defined as the potential for loss or damage when a threat exploits a vulnerability. Examples of risk include:
- Financial losses
- Loss of privacy
- Damage to your reputation Rep
- Legal implications
- Even loss of life
Reduce your potential for risk by creating and implementing a risk management plan. Here are the key aspects to consider when developing your risk management strategy:
- Assess risk and determine needs. When it comes to designing and implementing a risk assessment framework, it is critical to prioritize the most important breaches that need to be addressed. Although frequency may differ in each organization, this level of assessment must be done on a regular, recurring basis.
- Include a total stakeholder perspective. Stakeholders include the business owners as well as employees, customers, and even vendors. All of these players have the potential to negatively impact the organization (potential threats) but at the same time they can be assets in helping to mitigate risk.
- Designate a central group of employees who are responsible for risk management and determine the appropriate funding level for this activity.
- Implement appropriate policies and related controls and ensure that the appropriate end users are informed of any and all changes.
- Monitor and evaluate policy and control effectiveness. The sources of risk are ever-changing, which means your team must be prepared to make any necessary adjustments to the framework. This can also involve incorporating new monitoring tools and techniques.
Threat, vulnerability, and risk: an example
To summarize the concepts of threat, vulnerability, and risk, let’s use the real-world example of a hurricane. The threat of a hurricane is outside of one’s control. However, knowing that a hurricane could strike can help business owners assess weak points and develop an action plan to minimize the impact. In this scenario, a vulnerability would be not having a data recovery plan in place in the event that your physical assets are damaged as a result of the hurricane.
The risk to your business would be the loss of information or a disruption in business as a result of not addressing your vulnerabilities.

Leave A Comment?